What is a VPN and how does it work for data privacy?
VPN when connecting to a public wireless (Wi-Fi) network. In this way, the generated traffic travels encrypted and makes it difficult for a third party to steal confidential information. In this post, we will explain more about this type of network, some of its uses, encryption protocols, among other relevant information.
What is a VPN
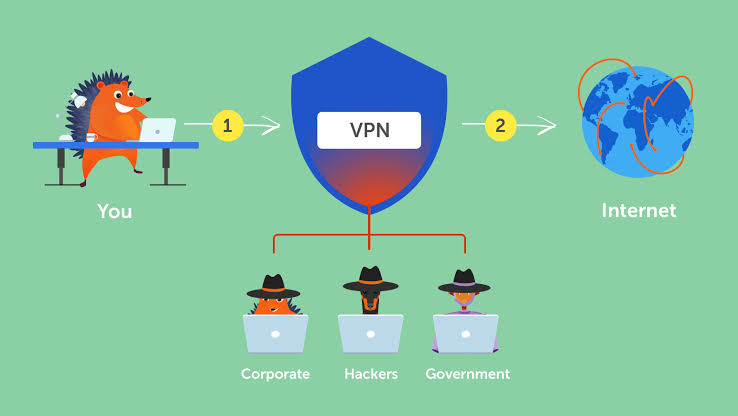
A VPN ( Virtual Private Network ) is a network technology used to connect one or more computers to a private network using the Internet. As we explained in the article about what a VPN trail is for , companies often use these networks so that their employees, from their homes, hotels, etc., can access corporate resources that they otherwise would not be able to. However, connecting an employee’s computer to corporate resources is only one function of a VPN.
VPN protocols
As you might guess, private and confidential information passes through a VPN that, in the wrong hands, could be detrimental to any company. This is further aggravated if the employee in question connects using unprotected public Wi-Fi. Fortunately, this problem can be mitigated by encrypting the data that is sent and received. In order to achieve this goal, the following protocols can be used:
IPsec ( Internet Protocol Security ): allows to improve security through robust encryption algorithms and a more exhaustive authentication system. IPsec has two encryption methods, transport mode and tunnel mode. It also supports 56 bit and 168 bit encryption (triple DES).
PPTP /MPPE: technology developed by a consortium made up of several companies. PPTP supports various VPN protocols with 40 bit and 128 bit encryption using the Microsoft Point to Point Encryption (MPPE) protocol. PPTP by itself does not encrypt information.
L2TP /IPsec (L2TP over IPsec): technology capable of providing the level of protection of IPsec over the L2TP tunnel protocol. Like PPTP, L2TP itself does not encrypt information .
Part of the protection of the information that travels through a VPN is encryption, however, verifying that it remains intact is just as important. To achieve this, IPsec uses a mechanism that if it detects any modification within a packet, it proceeds to discard it. Protecting the confidentiality and integrity of information using a VPN is a good measure for browsing public and insecure Wi-Fi even if you don’t want to access a corporate resource.
Finally, those home users who wish to use a VPN network can choose between free and paid services . It is important to mention that free ones usually work slower than one that is not. We also recommend reading our Wireless Network Security Guide which reviews other steps you can take to use a public wireless connection more securely.
Types of VPN
Now yes, we are going to see the two most common types of VPN and their main characteristics.
Client-based VPNs
This type of VPN networks allow a user to be connected to a remote network, through an application that is responsible for establishing communication and lifting the VPN. To access the secure connection, the user must run the application and authenticate with a username and password . In this way, the encrypted channel is created between the equipment and the remote network, for a secure exchange of data.
When we talk about the implementation of this type of VPN, we find that operating systems such as Windows, Mac, and mobile phones such as Android offer the possibility of configuring an encrypted communication channel with a network based on various standards. In the case of Apple and Windows family devices, options such as L2TP (Layer 2 Tunneling Protocol), PPTP or SSTP are included.
This type of VPN turns out to be a simple mechanism for users to connect their computers or mobile devices to a network in which the privacy of information must be guaranteed. In this way, it is a great option for an employee to connect to sensitive company information while working from home or from a hotel, for example.
Network-based VPNs
This approach is intended to connect different networks to each other through a network that is not secure, mainly the Internet . It is the approach chosen by companies to connect networks of different locations that are geographically separated to share information securely. There are several types of virtual private network networks. Within this approach we can find IPSec tunnels.
IPSec tunnels are the simplest approach to a VPN network and most network routers and firewalls have this feature. This type of approach is nothing more than establishing a tunnel ( tunneling ) so that all traffic exchanged between two networks travels encrypted. Although this same approach can be used to encapsulate traffic for a single device.
In this type of approach, it is necessary to establish the ends of the tunnel, that is, the devices in charge of encapsulating and decapsulating the information that travels encrypted. In addition, it is necessary to define how the authentication will take place (passwords or certificates) and the type of traffic that will flow through the established tunnel.
To define the traffic that can travel through the VPN, IPsec tunnels can have policies to restrict the traffic that flows through them. Access control lists (ACLs) are used to establish policy-based VPNs.
When using this type of approach, a single tunnel is established between two sites to provide access to resources in a more controlled manner. For example, it could be used to give a supplier or customer access to company-specific information.
In contrast to policy-based IPCSec tunnels, we find route-based IPsec tunnels that work as a virtual link and allow any type of traffic to flow through them.
There is no excuse not to protect communications
Whether you’re looking to protect access to a work network while traveling, protect browsing data when using public Wi-Fi, access geo-blocked sites, or bypass Internet censorship, using a VPN is the best alternative we have to guarantee that when exchanging our information it is done safely .
There are various VPN services that we can use to achieve our goal of guaranteeing the privacy of our data, we can choose from free alternatives or some that for a few dollars a month guarantee us the privacy we need. Of course, as with many other services, the free options make their profit on the other side, often the collection of personal and browsing data.
So, if you combine this protection measure with an anti-malware solution , a properly configured firewall and responsible behavior, as a user you can provide high levels of security for your information.